

CSPs' voice infrastructure is constantly facing massive network attacks from a broader spectrum of threat actors along with substantial fraudulent challenges. As an example, you can see the huge investments that have been made to secure computer data networks and email. Spam filters have developed to the point where it is rare for spam to be read, it is nearly always filtered out and most people know to ignore it in the rare cases it isn't caught. However, the same cannot be said for voice messages.
Based on Mobileum’s vast experience, expertise, and access to network information, its voice firewall can monitor the network to generate alerts, and control inbound and outbound voice network activity based on user-defined call admission control (CAC) policies, to do automatic blocking of illegal activities.
 According to the CFCA 2019 report, there has been a steady increase in telecom fraud; however, the ones that are increasing the most are the voice-related frauds. The growth in VoIP networks has introduced new vulnerabilities in the SIP protocol that are now being exploited along with SS7, diameter, and GTP to perpetrate voice fraud.
According to the CFCA 2019 report, there has been a steady increase in telecom fraud; however, the ones that are increasing the most are the voice-related frauds. The growth in VoIP networks has introduced new vulnerabilities in the SIP protocol that are now being exploited along with SS7, diameter, and GTP to perpetrate voice fraud.
These types of fraud and network attacks cannot be adequately addressed with traditional IP firewalls or Session Border Controllers (SBCs/eSBCs). If left unattended, these loopholes can lead to voice service disruption, impacting CSPs revenue, customer experience, government regulations, and overall network productivity. In the absence of an effective policy enforcement solution, CSPs will certainly witness massive fraudulent attacks.
 A session border controller (SBC) is a device regularly deployed in VoIP networks to exert control over the signaling and also the media streams required in setting up, conducting, and cutting down telephone calls or other interactive media communications.
A session border controller (SBC) is a device regularly deployed in VoIP networks to exert control over the signaling and also the media streams required in setting up, conducting, and cutting down telephone calls or other interactive media communications.
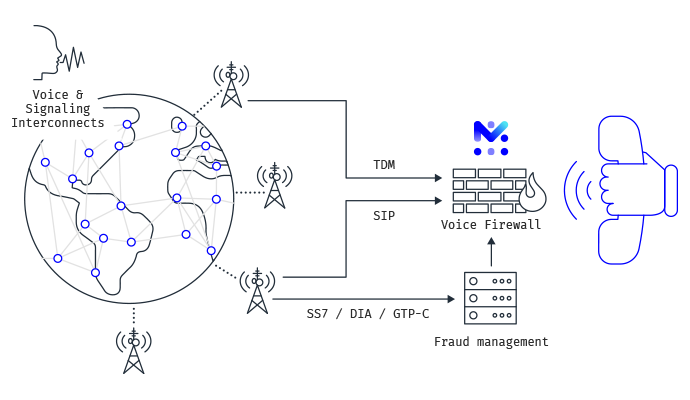
One of the problems with just relying on SBC for voice protection is that many communication networks still use TDM-based technology. Besides, these networks are often a mix of different vendor solutions, including multiple versions from the same vendor, resulting in a variety of signaling and media protocols such as MAP or Diameter, that need to be supported in the same call. For service provider networks experiencing a mix of Public Switched Telephone Network (PSTN) and Voice over Internet Protocol (VoIP) traffic, Mobileum’s Voice Firewall delivers in a single device the security functions that allow TDM and IP networks to deliver voice calls safely and secure.
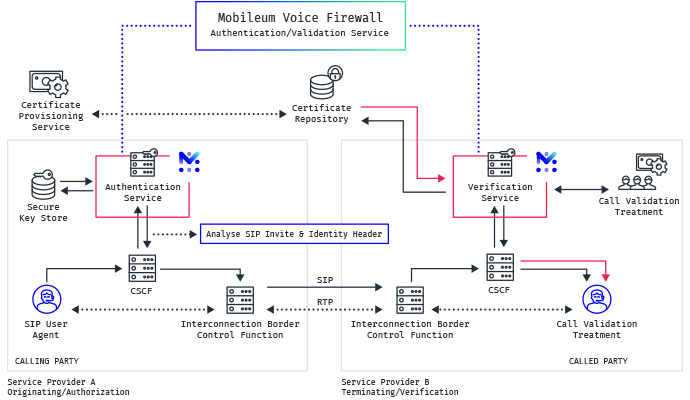 The increase in unwanted calls affects almost everyone with a phone in the United States nowadays. Even more disturbing are the calls where fraudsters hide their identity, by spoofing or changing the caller ID, using schemes to try to target or defraud consumers. The STIR and SHAKEN framework is at this stage the most reliable way to provide a mechanism of trust in the displayed caller name and number by authenticating the calling number.
The increase in unwanted calls affects almost everyone with a phone in the United States nowadays. Even more disturbing are the calls where fraudsters hide their identity, by spoofing or changing the caller ID, using schemes to try to target or defraud consumers. The STIR and SHAKEN framework is at this stage the most reliable way to provide a mechanism of trust in the displayed caller name and number by authenticating the calling number.
Our Voice Firewall leverages all of Mobileum’s expertise on national and international voice traffic, signaling security and fraud management expertise together with the STIR/SHAKEN framework, to ensure the calling number of a telephone call is secure without wrongly blocking or marking legit users or companies as spam.
 The first step towards dealing with voice fraud is its detection. As the first level of defense, Mobileum’s voice firewall can automatically scan through phone number databases, ranges, and destinations to determine “blacklist” callers. The second pillar of telecom anti-fraud measures is Mobileum’s fraud management system (FMS) advanced analytics. Most of the voice fraud schemes previously mentioned assume certain behavioral patterns that require further analytics without delaying calls. Learning to identify them in near real-time is the key to effective fraud prevention. Some examples of analytics for voice fraud detection include:
The first step towards dealing with voice fraud is its detection. As the first level of defense, Mobileum’s voice firewall can automatically scan through phone number databases, ranges, and destinations to determine “blacklist” callers. The second pillar of telecom anti-fraud measures is Mobileum’s fraud management system (FMS) advanced analytics. Most of the voice fraud schemes previously mentioned assume certain behavioral patterns that require further analytics without delaying calls. Learning to identify them in near real-time is the key to effective fraud prevention. Some examples of analytics for voice fraud detection include:
 The transition to All-IP requires “Gateways” to convert legacy signaling and traffic carried over TDM to new IP signaling and traffic carried over IP/Ethernet. The gateways must achieve synchronization between TDM circuits and IP networks and cope with impairments of the underlying networks. Most operators usually have national and international voice service planes. Both these services typically use TDM (ISUP), and SIP interconnects.
The transition to All-IP requires “Gateways” to convert legacy signaling and traffic carried over TDM to new IP signaling and traffic carried over IP/Ethernet. The gateways must achieve synchronization between TDM circuits and IP networks and cope with impairments of the underlying networks. Most operators usually have national and international voice service planes. Both these services typically use TDM (ISUP), and SIP interconnects.
Mobileum’s Voice Firewall handles both legacy, and IP interconnects, with the capability to communicate in CAMEL, INAP, and SIP/SIP-I, bringing the ability to understand the call routing, adding the capability of call context analysis to check for context miss behavior. i.e. An MT call, with a calling number which belongs to the country fixed-line number range, cannot reach the operator on the international mobile gateway.

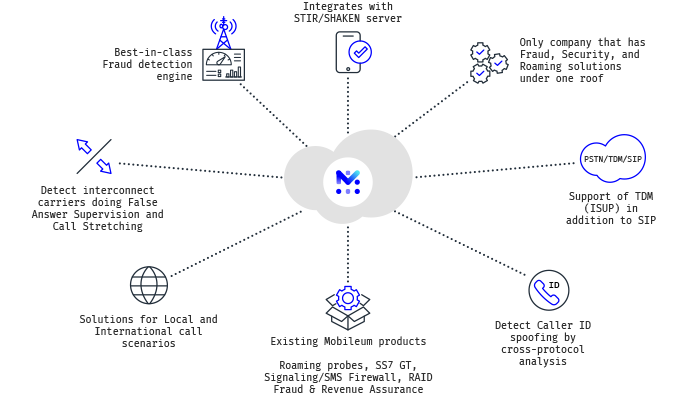 Mobileum Voice Firewall uses cross-protocol checks on the signaling of your VoIP traffic to prevent attacks, much faster than other solutions on the market that are just using CDR analysis. Any CSP can use our voice firewall as a bolt-on to their existing fraud management system to assure customer security. Mobileum leverages the power of its global deployments to make its solutions more effective. Our firewalls include an advanced threat intelligence capability to produce a worldwide defense to CSPs against attacks such as:
Mobileum Voice Firewall uses cross-protocol checks on the signaling of your VoIP traffic to prevent attacks, much faster than other solutions on the market that are just using CDR analysis. Any CSP can use our voice firewall as a bolt-on to their existing fraud management system to assure customer security. Mobileum leverages the power of its global deployments to make its solutions more effective. Our firewalls include an advanced threat intelligence capability to produce a worldwide defense to CSPs against attacks such as:
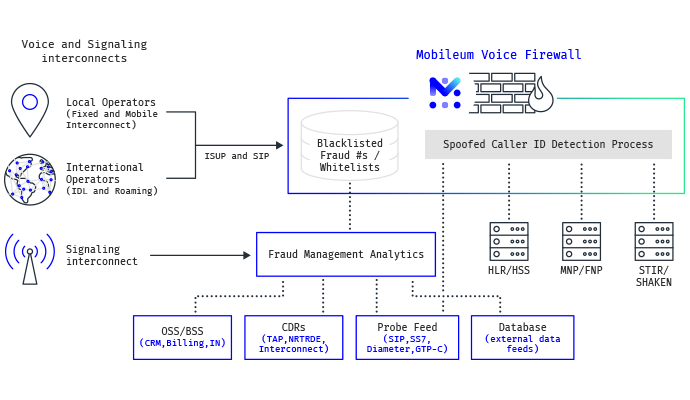
Because of the nature of the VoIP network, special care must be taken to ensure that the implementation of a firewall will allow voice communications to take place without compromising vital communications. Having that in mind, Mobileum has developed its voice firewall so that it can be deployed in a way that offers CSPs’ network the required level of protection, while at the same time not obstructing their VoIP communications by delivering the following capabilities:
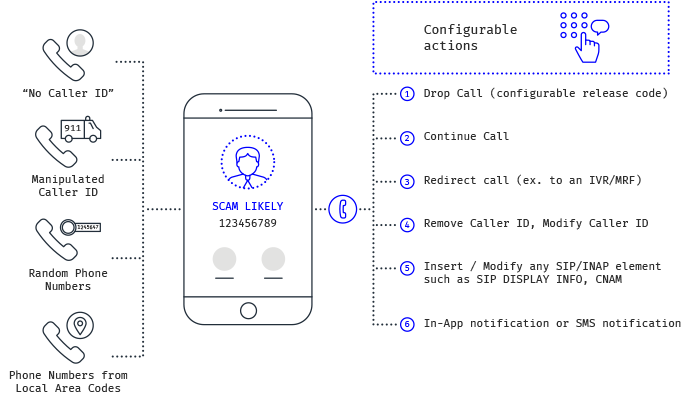 Nobody wants unwanted scam calls and spoofed robocalls. Phone scams are a real problem where your subscribers can lose a lot of money as well as it can damage the MNO brand perception. Just like with email spam blockers, anti-scam features need to deliver accurate filtering verdicts. To eliminate the possibility of good voice call being identified as spam (also known as false positives), our voice firewall offers the possibility to deliver the “Scam Likely” tag upon received calls. Using this feature, in case of doubt, operators do not just block all calls, since subscribers still receive them, just in case they’re real. That said, it’s very unlikely a real call will be tagged as a likely scam by our voice firewall, but it’ll still give your subscriber a heads up before they are about to answer a call from a known scammer’s phone number.
Nobody wants unwanted scam calls and spoofed robocalls. Phone scams are a real problem where your subscribers can lose a lot of money as well as it can damage the MNO brand perception. Just like with email spam blockers, anti-scam features need to deliver accurate filtering verdicts. To eliminate the possibility of good voice call being identified as spam (also known as false positives), our voice firewall offers the possibility to deliver the “Scam Likely” tag upon received calls. Using this feature, in case of doubt, operators do not just block all calls, since subscribers still receive them, just in case they’re real. That said, it’s very unlikely a real call will be tagged as a likely scam by our voice firewall, but it’ll still give your subscriber a heads up before they are about to answer a call from a known scammer’s phone number.
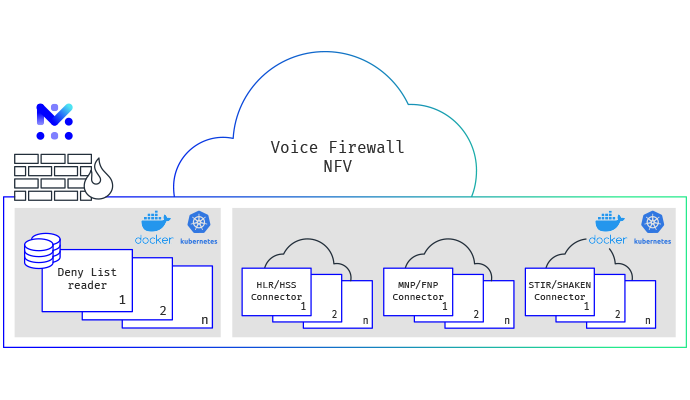
Network Function Virtualization (NFV) is gaining traction in enterprises and CSPs as it offers faster service enablement and easier deployment of applications which require consistency, determinism, and predictability. The nature of containers allows the deployment of microservices, where each part of a service is decomposed into a separate container to provide modular development, easy deployment, and scaling models.
Mobileum's Voice Firewall can be deployed in a containerized environment to enable a faster network function deployment and flexible implementation to match CSP's needs to have a programable network.
 Mobileum's Voice Firewall can be deployed in public or private cloud envinment. The use of a private cloud is now a common use for telco's network services. However, the use of a public envinment can bring to telcos lower operational costs than those associated to traditional networks, and the ability to bring services to market much quicker then before. Mobileum's voice firewall implementation brings all these capabilities to the MNO as part of a NaaS strategy.
Mobileum's Voice Firewall can be deployed in public or private cloud envinment. The use of a private cloud is now a common use for telco's network services. However, the use of a public envinment can bring to telcos lower operational costs than those associated to traditional networks, and the ability to bring services to market much quicker then before. Mobileum's voice firewall implementation brings all these capabilities to the MNO as part of a NaaS strategy.